A digital certificate, specifically an X.509 digital certificate, is a standardized electronic document that binds a public key to an identity. It's like a digital ID card, issued and signed by a trusted third party, the Certificate Authority (CA), to verify the authenticity of a public key.
[Read More]BLS signature scheme
Cryptography
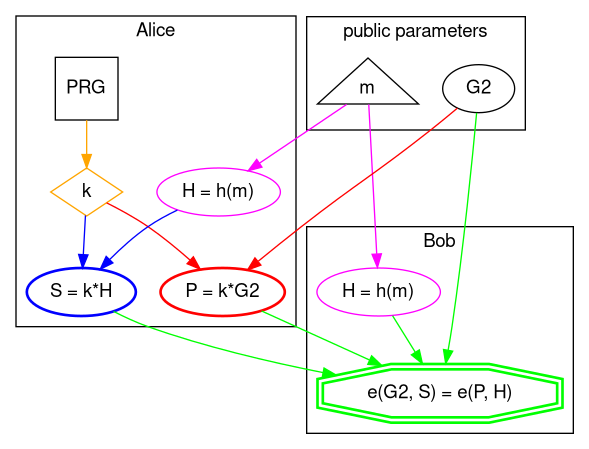
From a high level perspective this is how BLS (also known as Boneh–Lynn–Shacham) signature scheme works.
Hash functions
Cryptography
In simple terms, hash functions transform input data of arbitrary size (e.g. text, binary, etc) to fixed-length output (called hash value, hash code, fingerprint, message digest or simply hash) in a deterministic way. What else?
[Read More]Commitment schemes
Cryptography
A cryptographic commitment scheme is a way of committing to a statement without revealing the statement itself or reveal it at a later time.
[Read More]Elliptic curves
Cryptography
The easiest way to understand Elliptic Curve (EC), point addition, scalar multiplication and trapdoor function; explained with simple graphs and animations.
[Read More]Zero-knowledge proofs
Cryptography
Zero-knowledge is a method to prove that you know a secret ``x`` (e.g. a password, private key, piece of knowledge, etc) without revealing that secret.
[Read More]Zero-knowledge proofs
Cryptography
— layout: post title: "Zero-knowledge proofs" subtitle: Cryptography date: 2019-08-26 tags: ["cryptography", "zero-knowledge-proof", "math", "python", "zcash"] —
[Read More]EC-Schnorr
Cryptography
Overview
EC-Schnorr, as the name suggests, is a Schnorr-type digital signature scheme over elliptic curve, it's ECDSA's little sister and Schnorr's big brother implemented in the upcoming MuSig in Bitcoin.
[Read More]Schnorr
Cryptography
Schnorr is another digital signature scheme known for its simplicity, no division, no inversion, just plain old multiplication. Here is my simple 16 lines implementation in Python.
[Read More]ECDSA
Cryptography
Elliptic curve cryptography (ECC) and digital signature algorithm (ECDSA) are more complex than RSA or ElGamal but I will try my best to hide the hairy math and the implementation details.
[Read More]